07May
Every solution, regardless of its sophistication or purpose, inherently carries risks, including the potential for vulnerabilities. These risks can undermine user trust and compromise both personal and organizational data. However, by approaching these issues with openness and a commitment to security, there is a way to not only improve products but also strengthen the company's relationships with users. As a company committed to delivering high-quality and secure products, we encourage this approach.
This article will discuss hypothetical attack vectors on different parts of the Labyrinth Deception Platform, which includes Points, Admin Console, Workers, and Seeders. An example of how these components interact is:
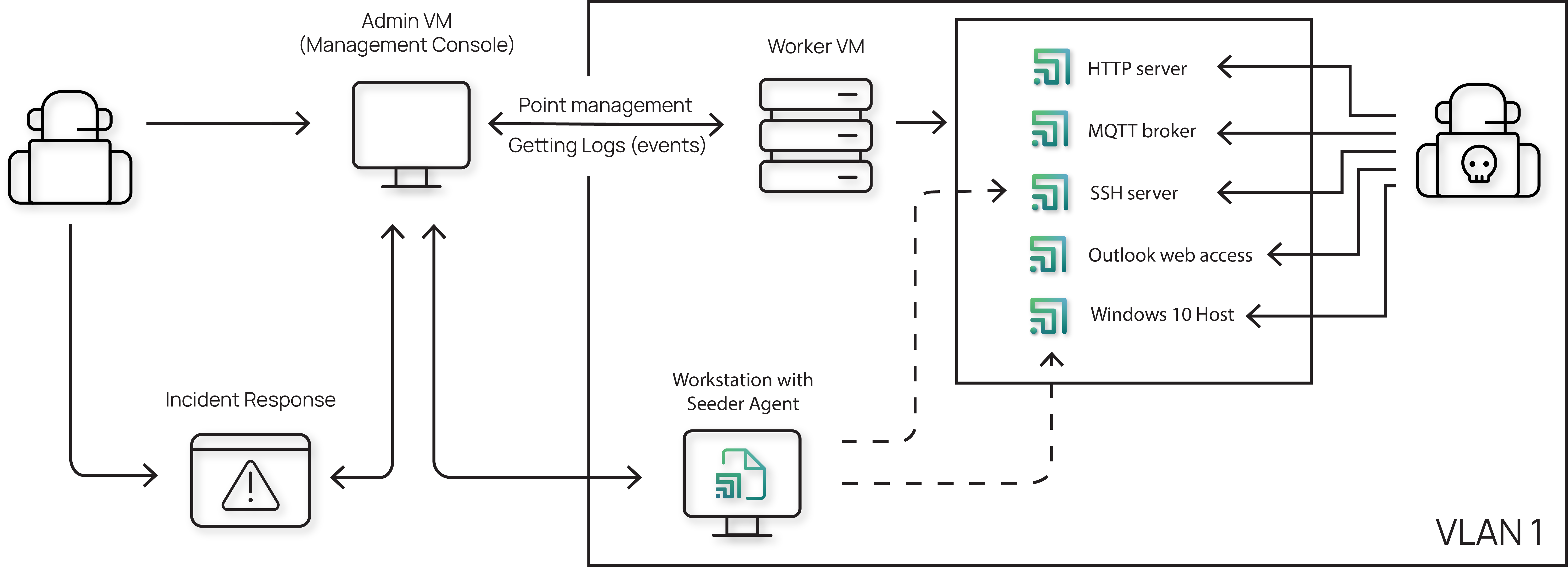
One primary and expected target for potential attacks is the Points. These are fully isolated instances, segregated from both the host system and other Points. Moreover, Points are continually monitored externally. Thus, any interaction by an attacker with a decoy, including connection attempts and subsequent hostile activities, will result in no more than an immediate alert to a Labyrinth operator.
Another point is the system's architecture. The platform uses a distributed setup with multiple virtual machines (VMs) that have specific roles: the Admin Node oversees the setup, and the Worker Nodes handle launching Points. It is important to note that all traffic between those Nodes is securely encrypted to ensure that sensitive information remains protected.
Even though Workers are nodes that are mostly exposed to danger, it is worth mentioning that they do not depend on each other; accessing one does not give access to another. What is more, those Nodes themselves do not have direct access to VLANs, which should be covered by deception. Each Point’s access to a VLAN is individually configured, ensuring separate access.
Finally, we will cover Seeder Agents, which are optional to use. These are special agents placed on real network hosts. The risk here is an attack through the communication channel between a Seeder Agent and the system. To handle this, Seeder Agents cannot be used without a Seeder Proxy, which acts as an additional decoy in Labyrinth and ensures a secure link between the real host and the Labyrinth system.

While no product can be entirely free of vulnerabilities, our commitment to rigorous security practices, transparency, and ongoing collaboration forms a robust defense against potential threats.
By covering the main starting points for hypothetical attacks, we ensure that the Labyrinth Deception Platform remains secure against the evolving landscape of threats. Additionally, we encourage you to test the platform yourself, giving you confidence in the system's resilience and providing you with a highly effective tool for securing your network.
