25Apr
1. NEW AND IMPROVED
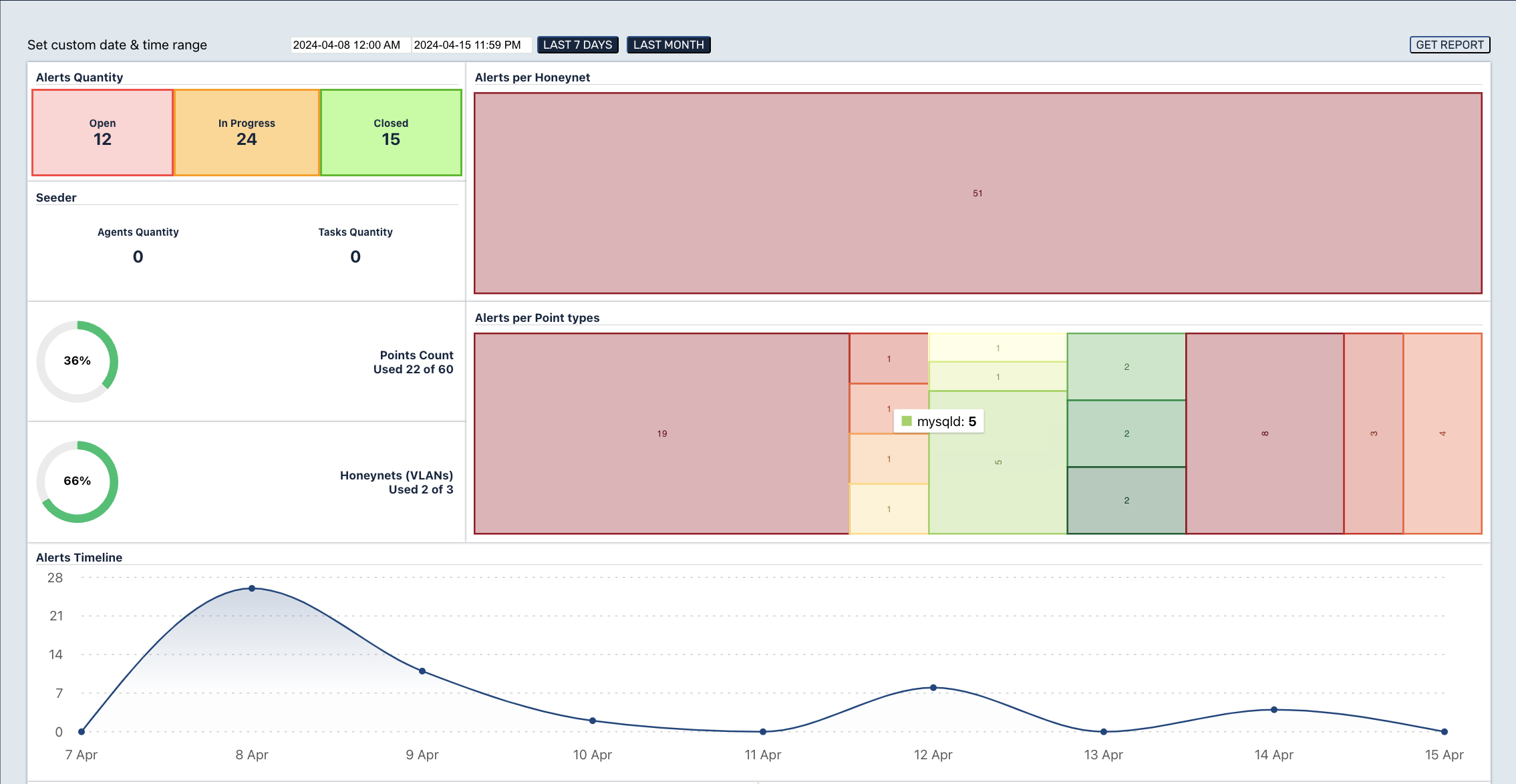
1.1. Improving the Dashboard
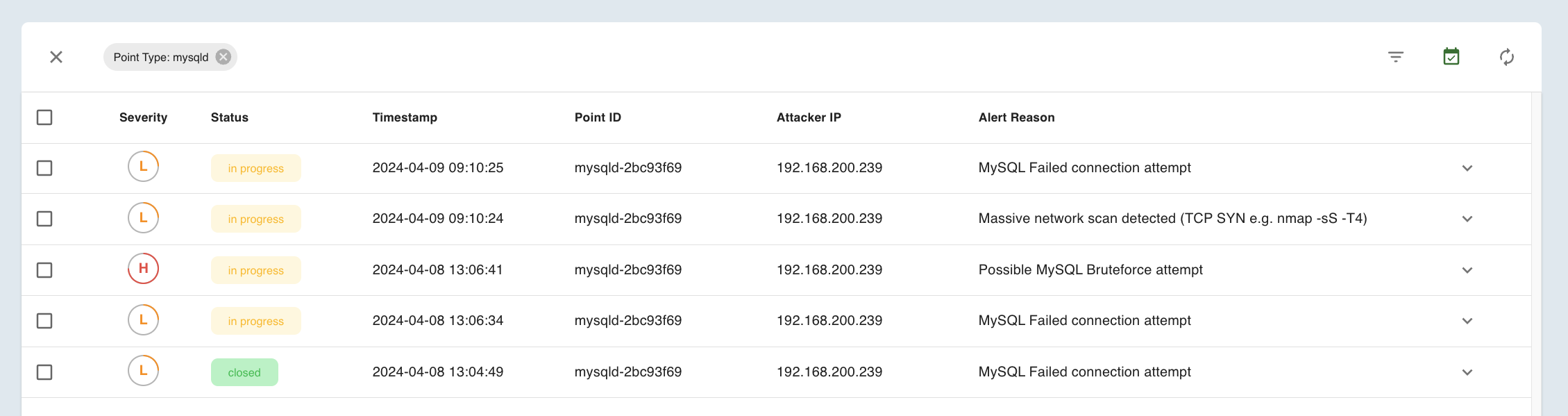
More interactivity has been added to the Dashboard. Now you can click on any dashboard element and go to the corresponding lists with applied filters.
For example, if you click on one of the Point Type indicators on the Alerts per Point Types dashlet, the user will be transferred to the list of alerts related to a particular Point Type.
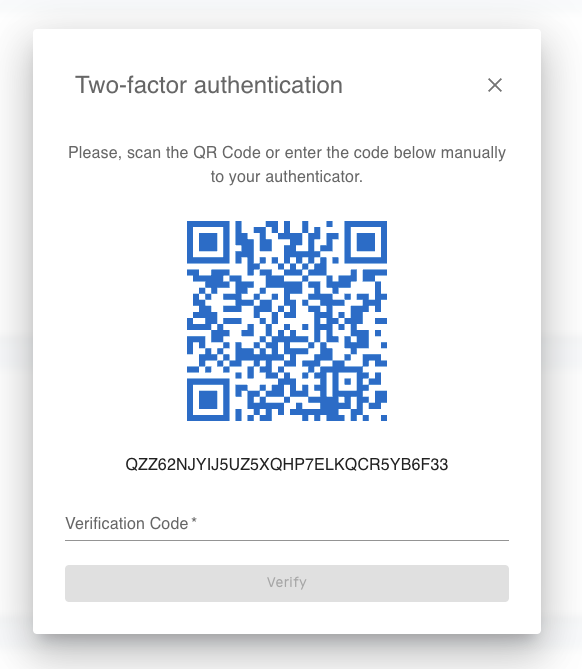
1.2. Multi-factor authentication (MFA)
In this release, it became possible to use MFA for user authentication. Any software or hardware that supports Time-based One-time Password (TOTP) is suitable as an authenticator. For example, Google Authenticator, Microsoft Authenticator, etc.
Each user in the system can connect a second authentication factor. If, for some reason, you need to disable or reset the MFA settings for a user, another user can do this: Superuser or Administrator.
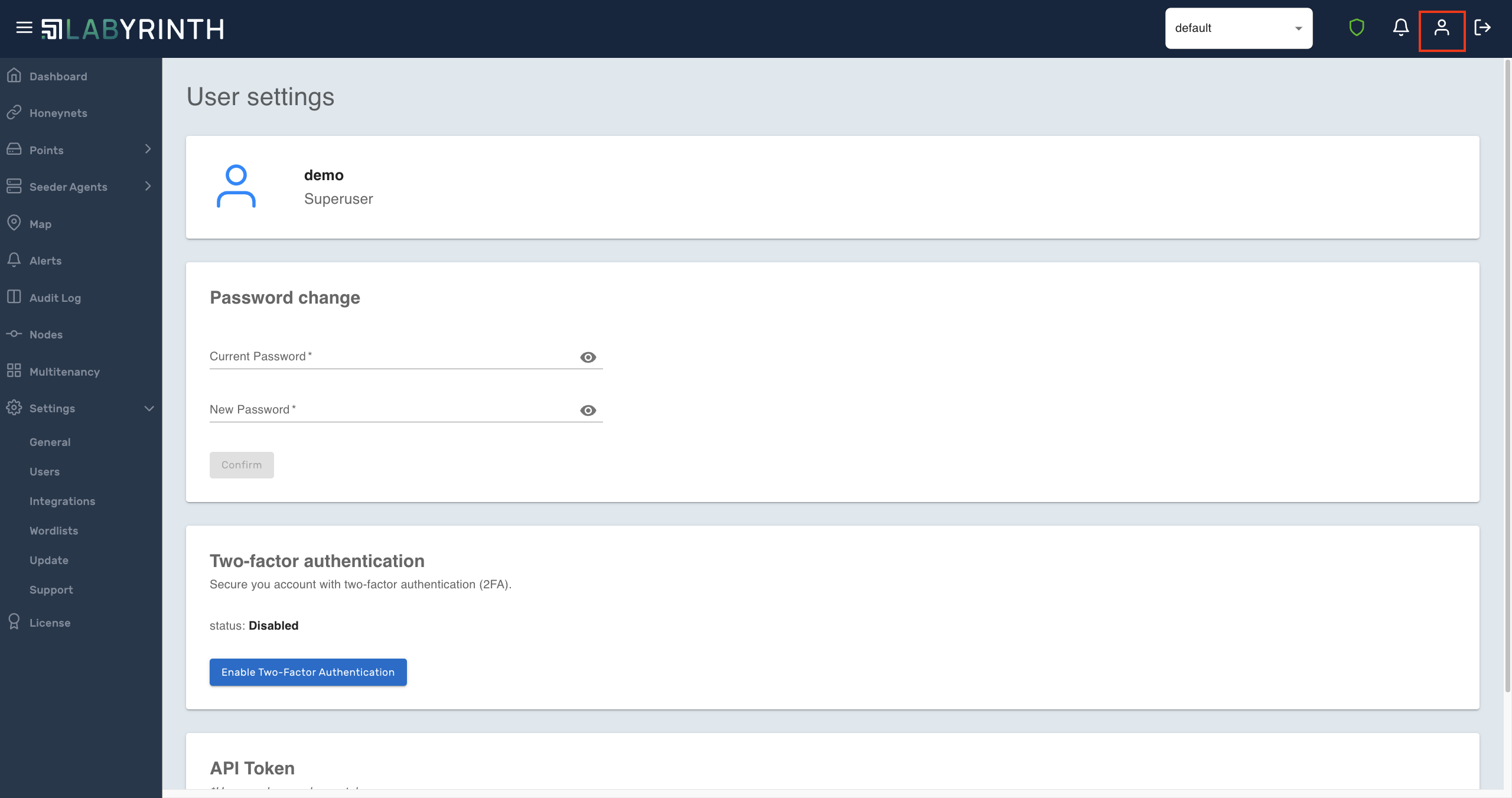
1.3. New user configuration view
Now you can get to the user settings through the user icon in the upper right corner.
Here the user can make the following settings:
- Change your current password
- Configuring MFA
- Generating a token API to interact with the API
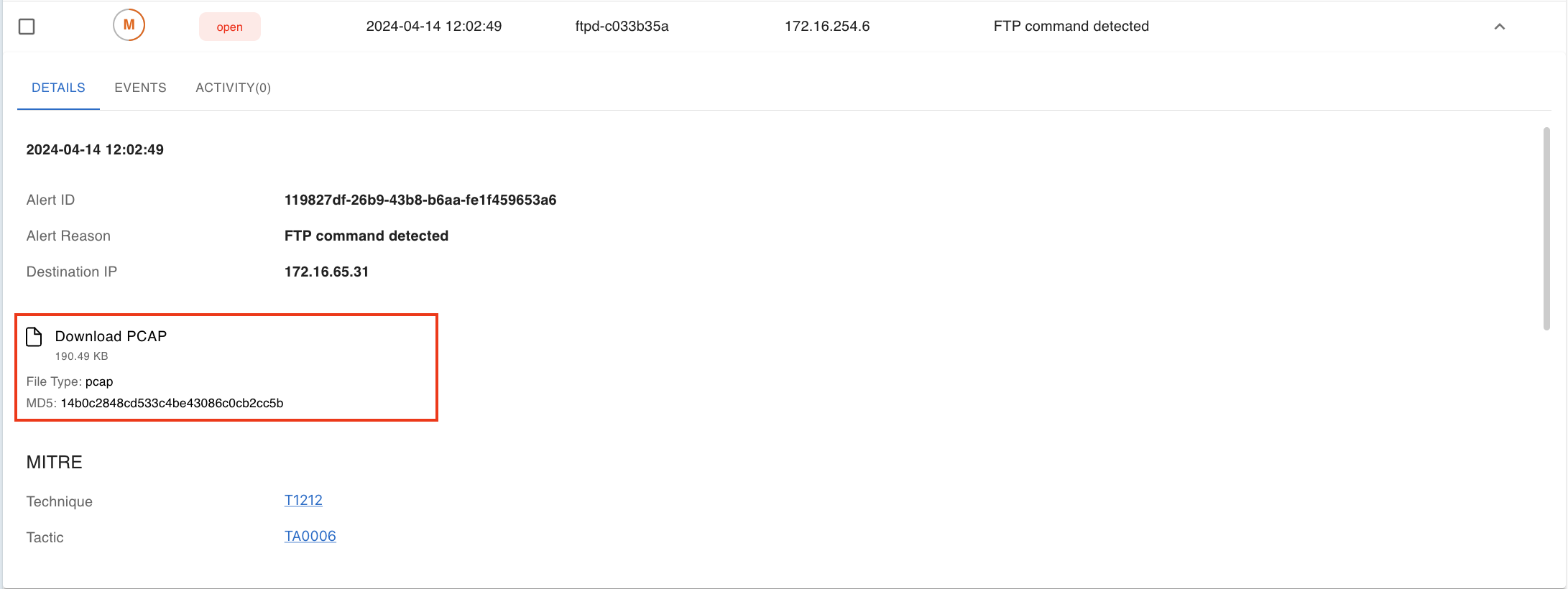
1.4. Dump network traffic for Alerts
A dump of network traffic is added to the alerts regarding network interaction. This dump is provided in PCAP format and can be read and processed using specialized software. For example, Wireshark, tshark, tcpdump and others.
Currently, a PCAP dump includes network traffic between the attacker's IP address and the Point's IP address that occurred when the alert was created.
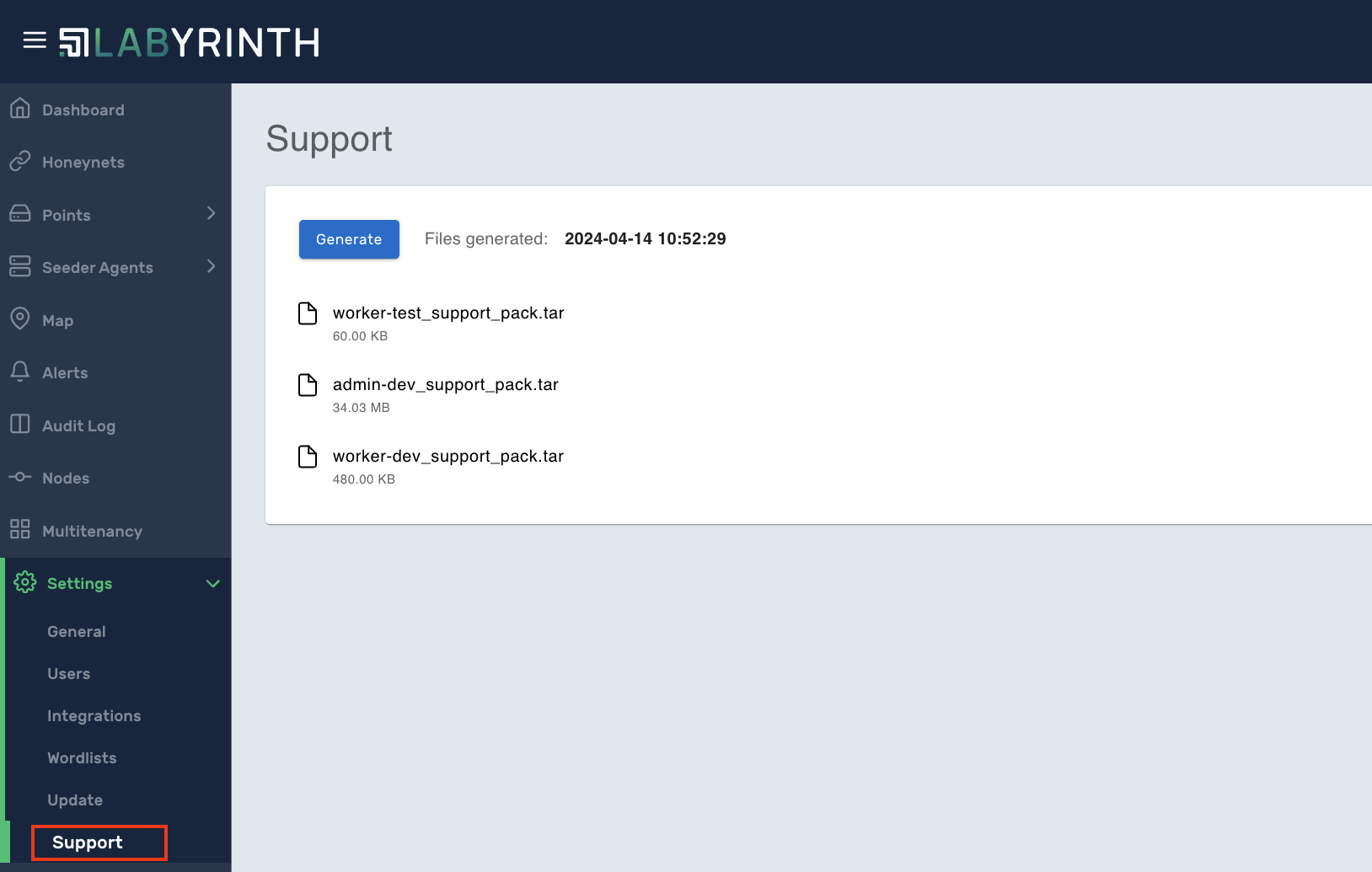
1.5. Log archive for technical support
Added the ability to form an archive of logs in order to simplify communication with support. The user can, upon request, form an archive necessary to solve a technical problem, download and provide this archive for analysis in support.
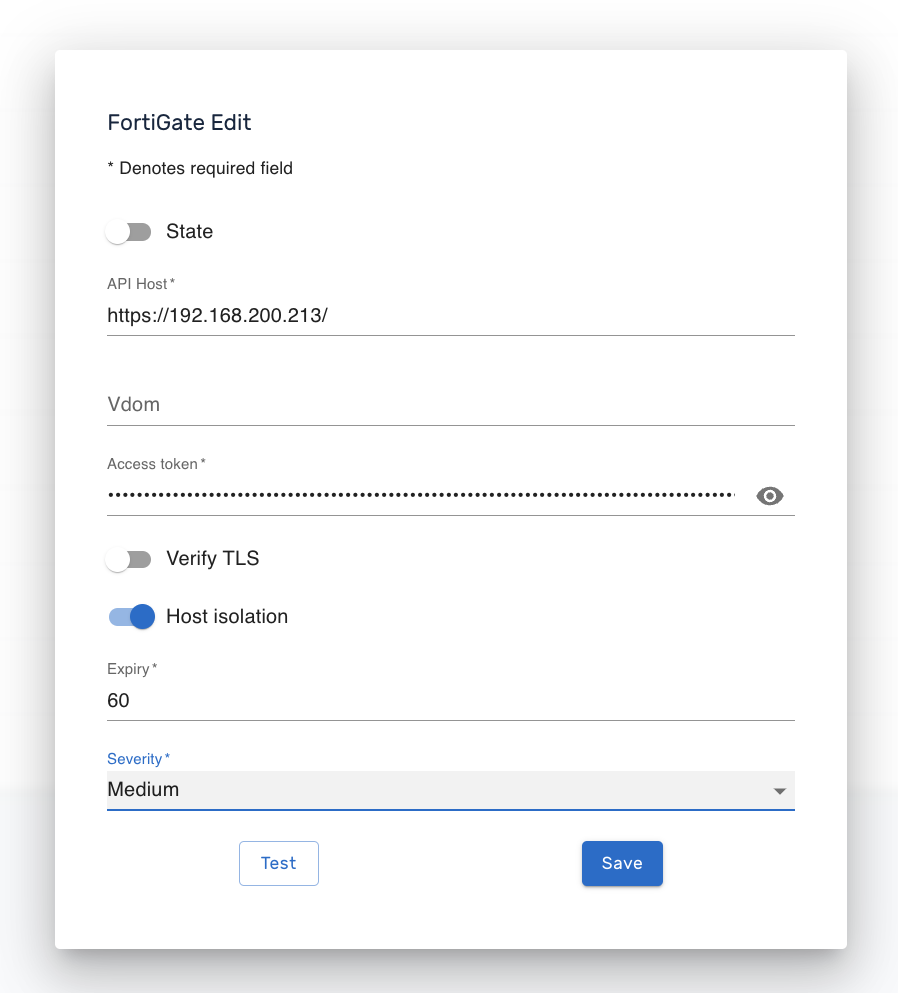
1.6. Improving integrations with FortiGate and CrowdStrike: configuring isolate mechanism
Configured integrations with FortiGate and Crowdstrike with isolate enabled worked when a new alert occurred. Currently, it is possible to set the lowest Severity level at which isolation will work.
For example, if any of the above integrations have the Severity level set to High, then the integration will only work on alerts from Severity High and Critical. At the same time, Medium and Low will be ignored by the isolate mechanism.
Also, for integration with FortiGate, the ability to set the time period for which the attacker's IP address will be quarantined has been added.
1.7. Admin VM (Management Console) in Azure Cloud
Prior to the release, only the Worker VM could be run on Azure Cloud. Previously, Azure Cloud had official support only for Worker Node. Now in this cloud you can deploy both Admin VM and Worker VM.
2. FIXES
2.1. Exceptions for Trusted IPs in FortiGate and CrowdStrike isolate
The isolate mechanism in integrations with FortiGate (block IP) and CrowdStrike (network containment) worked without taking into consideration exceptions for IP addresses in the Trusted IPs list. As a result, when simulating an attack from a trusted IP address, this address was blocked by FortiGate and CrowdStrike.
Currently, when implementing the isolate mechanism, the Trusted IPs list is taken into account and such addresses are not blocked.
2.2. TLS Certificate Validation
Fixed a bug with TLS certificate validation in Settings -> General -> SSL/TLS Certificate, as a result of which it was impossible to upload a new TLS certificate for the web interface.
2.3. Error when updating the statuses of Nodes and their services
Fixed a bug that could result in data on the status of a Node and its services being irrelevant. This could manifest itself when one of the nodes was unavailable.
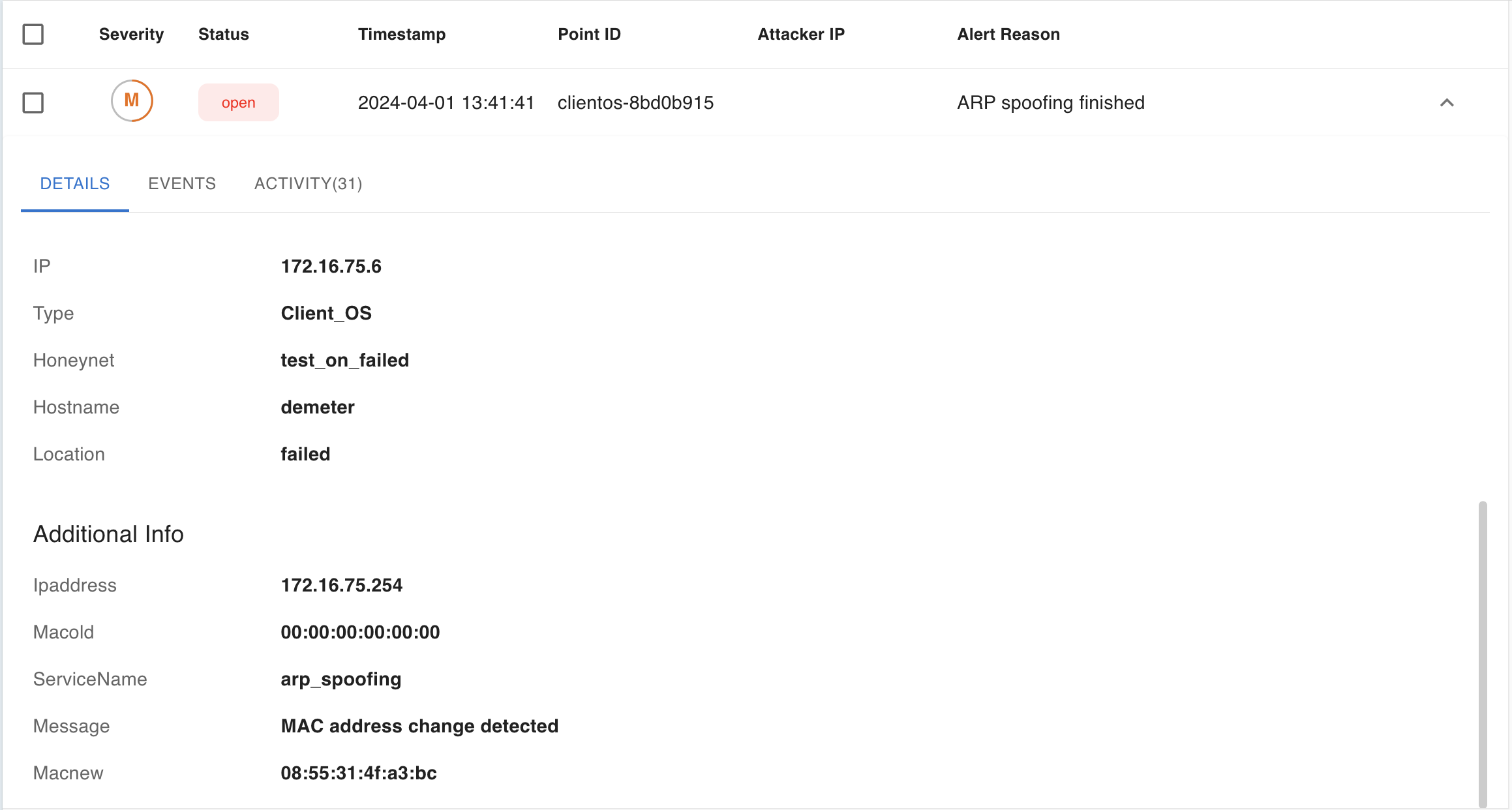
2.4. False-positive ARP spoofing alert
When using a Client OS Point in the Honeynet of the DHCP type a false-positive alert could occur, indicating ARP spoofing. This issue was fixed in this release.
2.5. Dynamic data update in Extend Disk Size menu in the pseudographic interface
In the pseudographical interface, accessible through the console or SSH, there was an issue where the display of available free disk space for expanding disk partitions did not update during the "hot" expansion of a virtual machine's disk (i.e., without rebooting). This issue has been resolved, ensuring that the data reflecting free disk space is now accurately updated in real-time, without the need to reboot the virtual machine.
2.6. Missing Attacker IP Address in Alert Notifications from SMTP Integration
We have resolved a bug that previously omitted the attacker's IP address in email notifications triggered by new alerts due to SMTP integration.